MongoDB Federated Authentication links your credentials across MongoDB systems like MongoDB Support, MongoDB University, MongoDB Atlas, MongoDB Cloud Manager, MongoDB Community Forums, and MongoDB Feedback. Atlas implements authentication using the Federated Identity Management model.
Using the FIM model:
Your company manages your credentials using an Identity Provider (IdP). With its IdP, your company can enable you to authenticate with other services across the web.
You configure MongoDB Atlas to authenticate using data passed from your IdP.
This goes beyond SSO as your IdP manages your credentials, not MongoDB. Your users can use Atlas without needing to remember another username and password.
Important
While you have a federated IdP enabled, Atlas disables any other authentication mechanisms.
The following procedure walks you through linking a SAML IdP to Atlas.
Required Access
To manage federated authentication, you must have
Organization Owner access to one or more organizations that are
delegating federation settings to the instance.
Procedure
Important
Two-Stage Configuration
Depending on your Identity Provider, some circular logic may apply when linking it to a Service Provider like Atlas. To link your IdP to Atlas:
Your IdP needs values from Atlas and
Atlas needs values from your IdP.
To simplify setup, Atlas prompts you to enter placeholder values for the IdP and Atlas configurations. You will replace these values later in the procedure.
Configure An External Identity Provider Application
To configure Federated Authentication, you must have an external SAML IdP application. In the SAML IdP, you must perform the following:
Create a new application for Atlas.
Configure initial SAML values for the new application:
Set placeholder values for the following fields:
SP Entity ID or Issuer
Audience URI
Assertion Consumer Service (ACS) URL
Set valid values for the following fields:
FieldValueSignature Algorithm
Algorithm used to encrypt the IdP signature. Atlas supports the following signature algorithm values:
SHA-1SHA-256
Name ID
Valid email address.
IMPORTANT: Name ID is used as both the email address and the username of your Atlas user account.
Name ID Format
urn:oasis:names:tc:SAML:1.1:nameid-format:unspecifiedurn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
Create attributes with the following Attribute Names for the following SAML Attribute Values:
SAML Attribute NameSAML Attribute ValuefirstNameFirst Name
lastNameLast Name
memberOfUser Groups
Note
The names of these attributes are case sensitive. Type these attribute names as shown in camelCase.
Save these values.
Once you have completed the initial setup for your IdP application, you link the IdP to Atlas to federate your users' logins.
Apply Your Identity Provider to Atlas
Note
Prerequisite
This procedure assumes you already have an external IdP. To learn how to configure an IdP, see Configure An External Identity Provider Application.
You can configure Federated Authentication in Atlas from the Federation Management Console. Use this console to:
Configure Identity Providers to authenticate users belonging to specified organizations.
Connect Atlas Organizations to your IdP.
Verify and associate Domains with your IdP to force users to authenticate using that IdP.
Open the Management Console
In Atlas, go to the Federation Management console for your organization.
If it's not already displayed, select your desired organization from the Organizations menu in the navigation bar.
In the sidebar, click Federation under the Identity & Access heading.
Click Open Federation Management App.
The Federation page displays.
From the Management Console:
Click Configure Identity Providers.
If you do not have any Identity Providers configured yet, click Setup Identity Provider. Otherwise, on the Identity Providers screen, click Add Identity Provider.
Enter or select the following SAML Protocol Settings.
FieldNecessityDescriptionConfiguration Name
Required
Human-readable label that identifies this configuration.
Configuration Description
Optional
Human-readable label that describes this configuration.
IdP Issuer URI
Required
Identifier for the issuer of the SAML Assertion.
Specify a placeholder value for this field. Obtain the real value for this field from your IdP once you have supplied it with the Atlas metadata.
IdP Single Sign-On URL
Required
URL of the receiver of the SAML AuthNRequest.
Specify a placeholder value for this field. Obtain the real value for this field from your IdP once you have supplied it with the Atlas metadata.
IdP Signature Certificate
Required
PEM-encoded public key certificate of the IdP. You can obtain this value from your IdP.
You can either:
Upload the certificate from your computer, or
Paste the contents of the certificate into a text box.
Request Binding
Required
SAML Authentication Request Protocol binding used to send the AuthNRequest. Can be either:
HTTP POSTHTTP REDIRECT
Response Signature Algorithm
Required
Response algorithm used to sign the SAML AuthNRequest. Can be either:
SHA-256SHA-1
Click Next.
Configure Your Identity Provider with Atlas Metadata
Having set up your IdP in Atlas, you can provide the required Atlas metadata to your IdP.
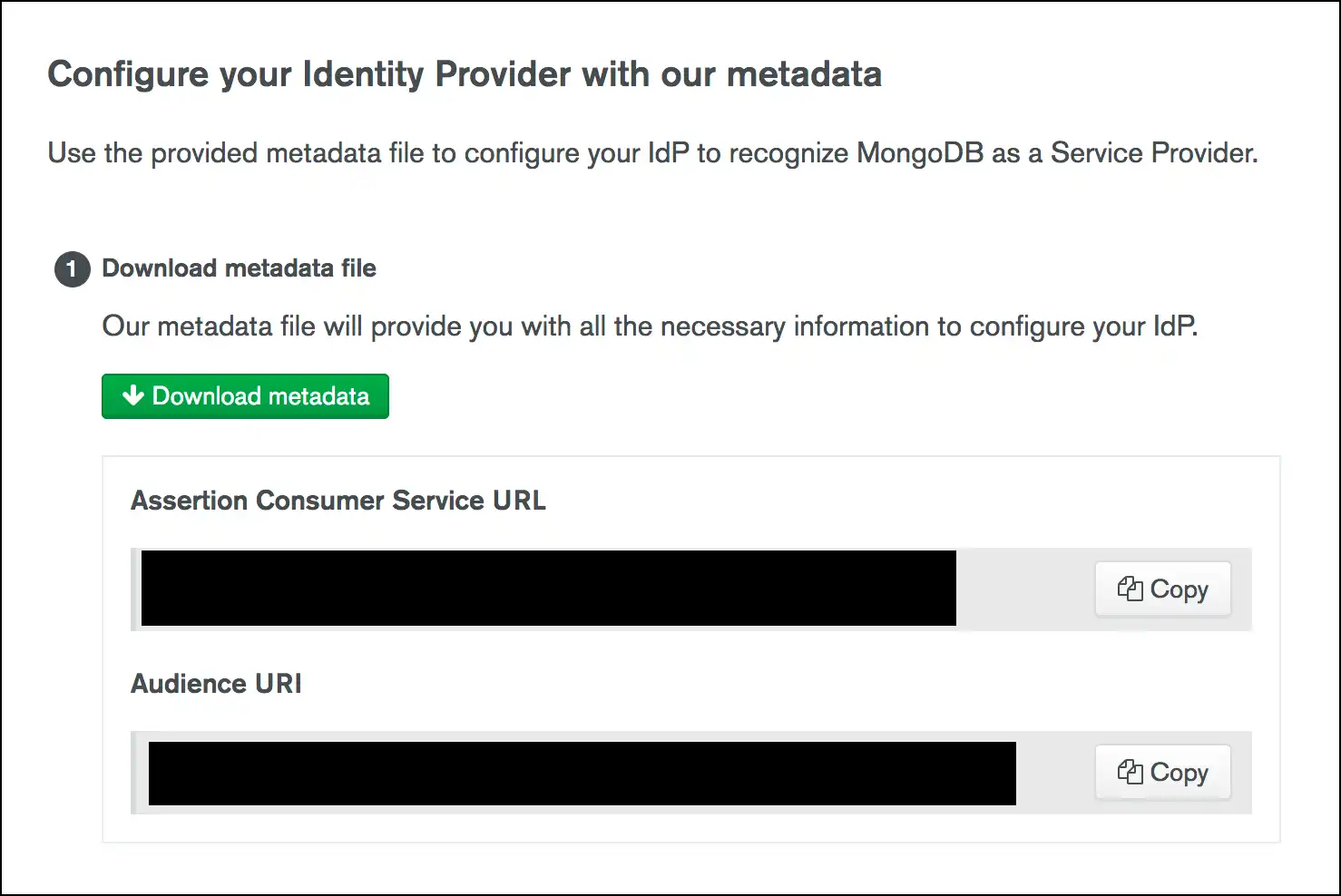
On the Identity Provider screen in Atlas, click Download metadata to download the metadata required by your IdP. Atlas provides the data as an
.xmlfile.![Image showing how to download metadata]()
Note
Atlas provides the Assertion Consumer Service URL and Audience URI if you wish to manually copy and save these values. These values are included in the metadata download.
Note
The SAML trust model requires certificate exchange over trusted channels during setup and doesn't require CA-signed certificates. During federated authentication, all traffic between MongoDB Atlas and the browser runs over TLS using a CA-signed certificate. Therefore,
metadata.xmlprovides only a self-signed certificate for request signing and signature validation.Upload the metadata to your IdP.
You now have the necessary information to replace the placeholder IdP Issuer URI and IdP Single Sign-On URL values set when you set up the initial IdP mapping in Atlas.
In Atlas, modify the placeholder values set for IdP Issuer URI and IdP Single Sign-On URL for the linked IdP with the proper values from your IdP.
Optionally, add a RelayState URL to your IdP to send users to a URL you choose and avoid unnecessary redirects after login. You can use:
DestinationRelayState URLMongoDB Atlas
Login URL generated for your identity provider configuration in the Atlas Federation Management App.
MongoDB Support Portal
https://auth.mongodb.com/app/salesforce/exk1rw00vux0h1iFz297/sso/saml MongoDB University
https://auth.mongodb.com/home/mongodb_thoughtindustriesstaging_1/0oadne22vtcdV5riC297/alndnea8d6SkOGXbS297 MongoDB Community Forums
https://auth.mongodb.com/home/mongodbexternal_communityforums_3/0oa3bqf5mlIQvkbmF297/aln3bqgadajdHoymn297 MongoDB Feedback Engine
https://auth.mongodb.com/home/mongodbexternal_uservoice_1/0oa27cs0zouYPwgj0297/aln27cvudlhBT7grX297 MongoDB JIRA
https://auth.mongodb.com/app/mongodbexternal_mongodbjira_1/exk1s832qkFO3Rqox297/sso/saml Return to Atlas and click Finish.
Important
Once you link your IdP to Atlas, it shows as Inactive in the Federation Management Console until you map at least one domain to the IdP.
Next Steps
After you successfully linked your IdP to Atlas, you must map one or more domains to your Identity Provider. Atlas authenticates users from these domains through your IdP.