The Authentication tab allows you to connect to deployments that require authentication. To learn about authentication mechanisms within MongoDB, see Authentication Mechanisms.
Procedure
Click the Authentication tab.
Select your authentication method from the following options:
Username / Password
Provide the following information:
Username
Password
(Optional) Authentication Database
Authentication Mechancism:
Default
The
Defaultsetting selects the first authentication mechanism supported by the server according to an order of preference.With the
Defaultsetting, MongoDB tries to authenticate using the following mechanisms in the order they are listed:SCRAM-SHA-256SCRAM-SHA-1MONGODB-CR
OIDC
Select OIDC if the deployment uses OpenID Connect as its authentication mechanism.
Note
By default, Compass requests the oidc and offline_access
scopes from the identity provider (IdP). If the IdP supports neither
oidc nor offline_access, Compass does not request
those scopes. If the IdP supports oidc but not offline_access,
you must re-authenticate frequently. To learn more, see
oidcIdentityProviders Fields.
Provide the following information:
Field | Description |
|---|---|
Username | Optional. OpenID Connect username. |
Auth Code Flow Redirect URI | Optional. Specify a URI where the identity provider redirects you after authentication.
The URI must match the configuration of the Identity Provider.
The default is |
Consider Target Endpoint Trusted | Optional. Allows connecting to a target endpoint that is not in the list of endpoints that are considered trusted by default. Use to ensure that access tokens are sent to trusted servers. Only use this option when connecting to servers that you trust. |
Enable Device Authentication Flow | Optional. When the Show Device Auth Flow Checkbox setting is enabled, Compass can provide you with a URL and code to finish authentication. This is a less secure authentication flow that can be used as a fallback when browser-based authentication is unavailable. |
Use Application-Level Proxy Settings | Optional. Use the application-level proxy settings specified in the Compass Settings panel. Enabled by default. If you don't enable application-level proxy settings, Compass uses the same proxy to connect to both the cluster and identity provider. |
Send a nonce in the Auth Code Request | Optional. Includes a random nonce as a part of the auth code request to prevent replay attacks. Enabled by default. The nonce is an important security component. Only disable this setting if it is not supported by your OIDC provider. |
X.509
Select X.509 if the deployment uses X.509 as its authentication mechanism.
Note
X.509 Authentication requires a client certificate. To enable TLS and add a client certificate, see the TLS / SSL tab in Compass.
Kerberos
Select Kerberos if the deployment uses Kerberos as its authentication mechanism.
Provide the following information:
Field | Description | ||||||
|---|---|---|---|---|---|---|---|
Principal | Every participant in the authenticated communication is known as a "principal", and every principal must have a unique name. | ||||||
(Optional) Service Name | |||||||
(Optional) Canonicalize Host Name | Kerberos uses the canonicalized form of the host name | ||||||
(Optional) Service Realm | The service realm is the domain over which a Kerberos authentication server has the authority to authenticate a user. If you choose to Canonicalize Host Name, you can specify one of the following options:
For more information on principal name canonicalization in Kerberos, see this RFC document. | ||||||
(Optional) Provide password directly | Used to verify your identity. To show the Kerberos password field, you must enable the showKerberosPasswordField option. |
Authenticate as a Different Kerberos User on Windows
When you authenticate with Kerberos on Windows, the Principal you specify must match the principal of the security context that Compass is running. Normally, this is the logged-in user who is running Compass.
To authenticate as a different Kerberos user, run MongoDB Compass as the chosen user and specify the Principal for that user. To run MongoDB Compass as a different user, either:
Hold Shift and right-click the MongoDB Compass program icon to select Run as a different user.
Use the
runascommand-line tool. For example, the following command runs MongoDB Compass as a user namedadmin:runas /profile /user:mymachine\admin <path to MongoDB Compass>
After you start MongoDB Compass as the chosen user, to authenticate against your Kerberos-enabled MongoDB deployment, specify the Principal for the corresponding user.
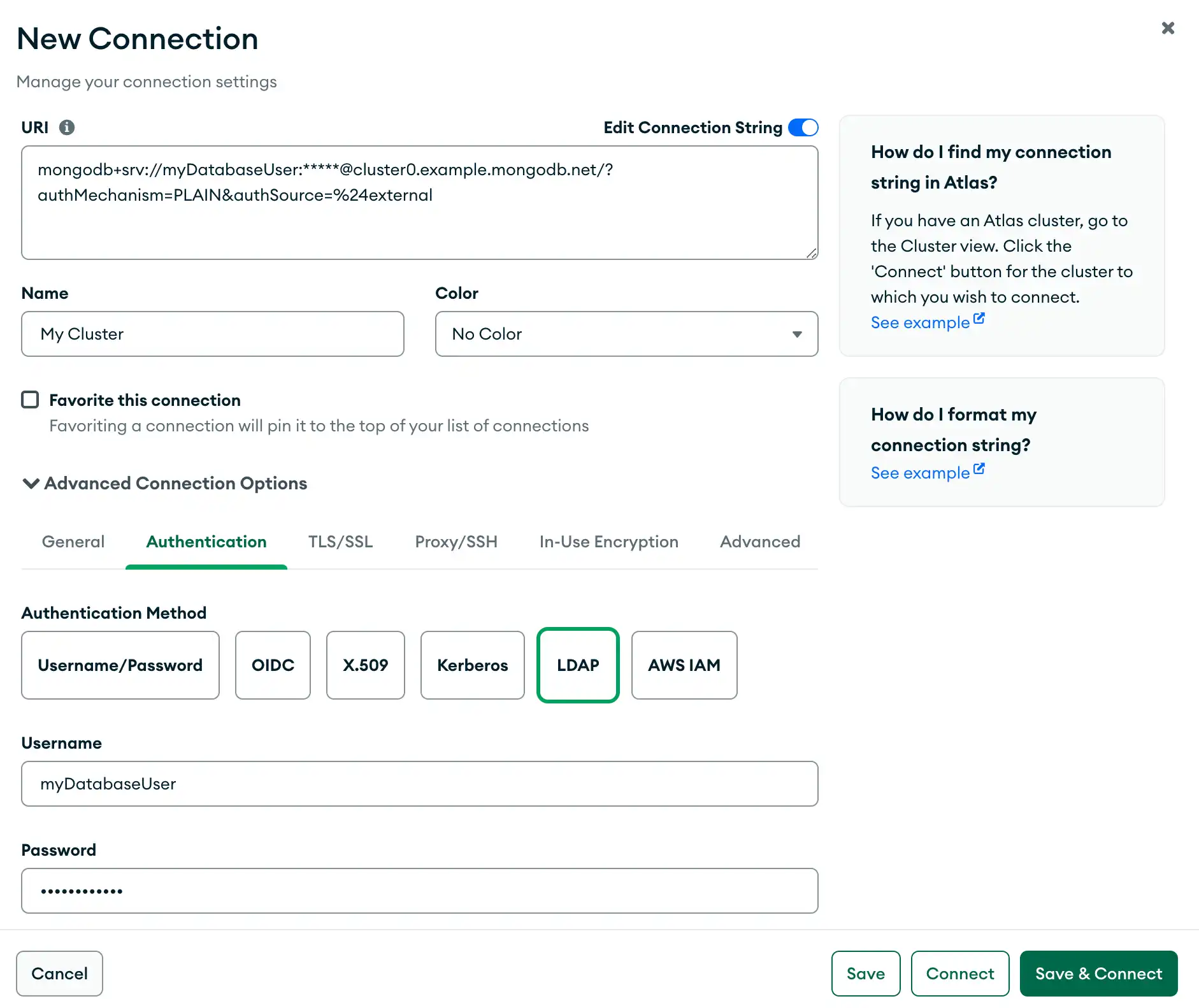
LDAP
Note
See the Examples section on this page for an example of the authentication tab configured for username and password authentication.
Select LDAP if the deployment uses LDAP as its authentication mechanism.
Provide the following information:
Username
Password
AWS IAM
Select AWS IAM if the deployment uses AWS IAM as its authentication mechanism.
The following fields are optional as they can be defined on your platform using their respective AWS IAM environment variables. MongoDB Compass will use these environment variable values to authenticate; you do not need to specify them in the connection string.
(Optional) AWS Access Key Id
(Optional) AWS Secret Access Key
(Optional) AWS Session Token
(Optional) For advanced connection configuration options, click the Advanced tab.
Tip
To disconnect from your deployment, see Disconnect from MongoDB.
Examples
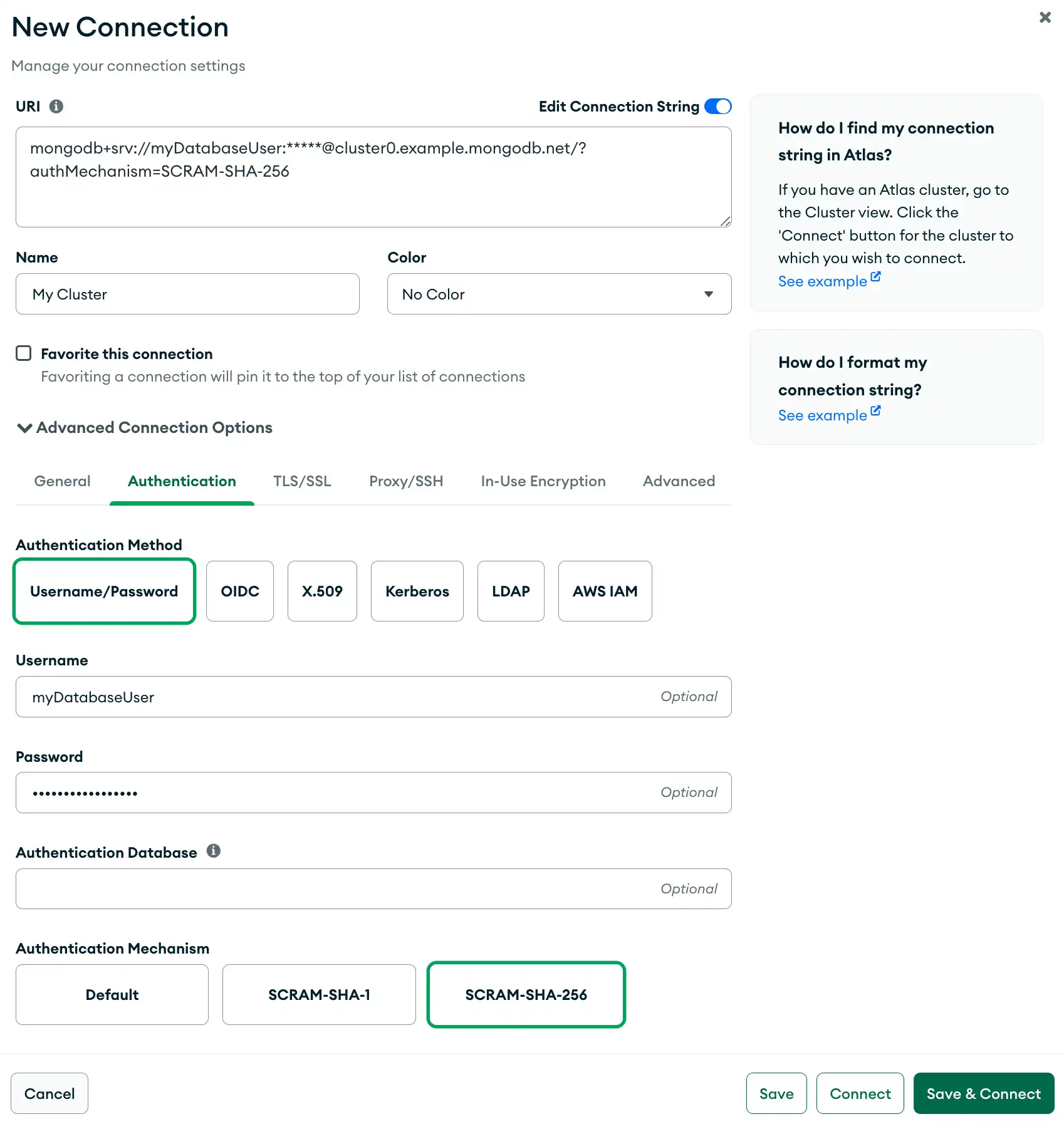
Username and Password Authentication
The following example specifies a connection with username and password authentication with SCRAM-SHA-256 in the Authentication tab.
LDAP Authentication
Alternatively, the following example specifies a connection with LDAP authentication in the Authentication tab.