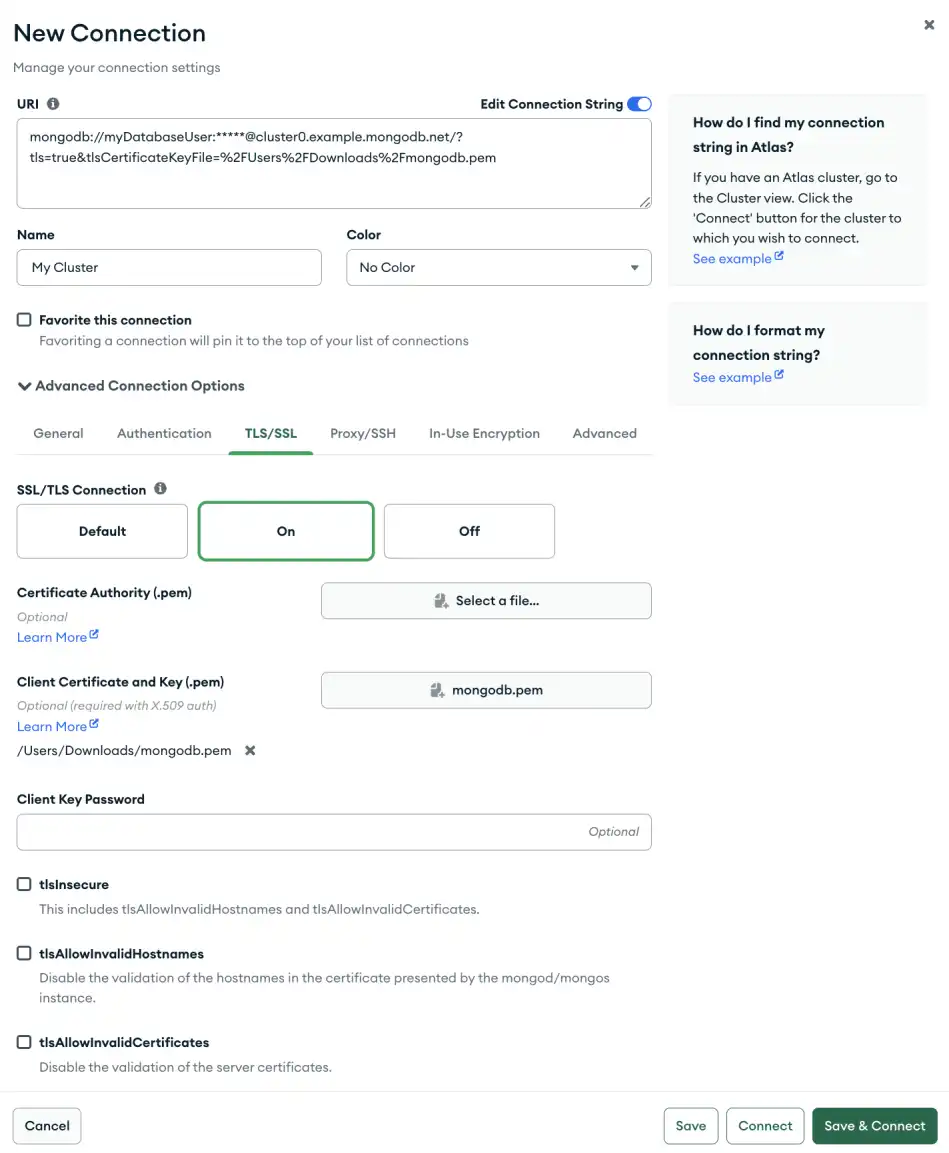
The TLS / SSL tab allows you to connect deployments with TLS / SSL. For more information on TLS / SSL, see TLS Options
Note
If you connect to an Atlas cluster with the standard connection string format, you must enable TLS/SSL.
Procedure
Click the TLS / SSL tab.
You can leave TLS unset with the Default option or set the TLS / SSL
connection On or Off.
Option | Description |
|---|---|
Default | The |
On | Select the |
Off | The Enable TLS / SSL to avoid security vulnerabilities. |
Additional TLS / SSL Options
When TLS is On you can specify the following:
Option | Description |
|---|---|
Certificate Authority | One or more certificate files from trusted Certificate Authorities to validate the certificate provided by the deployment. |
Client Certificate | Specifies the location of a local .pem file that contains either the client's TLS/SSL X.509 certificate or the client's TLS/SSL certificate and key. |
Client Key Password | If the Client Private Key is protected with a password, you must provide the password. |
tlsInsecure | Disables various certificate validations. |
tlsAllowInvalidHostnames | Disables hostname validation of the certificate presented by the the deployment. |
tlsAllowInvalidCertificates | Disable the validation of the server certificates. |
Warning
Enabling tlsInsecure, tlsAllowInvalidHostnames, and
tlsAllowInvalidCertificates may cause a security
vulnerabilty.
(Optional) For advanced connection configuration options, click the Advanced tab.
Tip
To disconnect from your deployment, see Disconnect from MongoDB.
Example
The following example specifies a connection with TLS/SSL enabled in the TLS / SSL tab. This connection uses X.509 authentication which requires a client certificate.
1