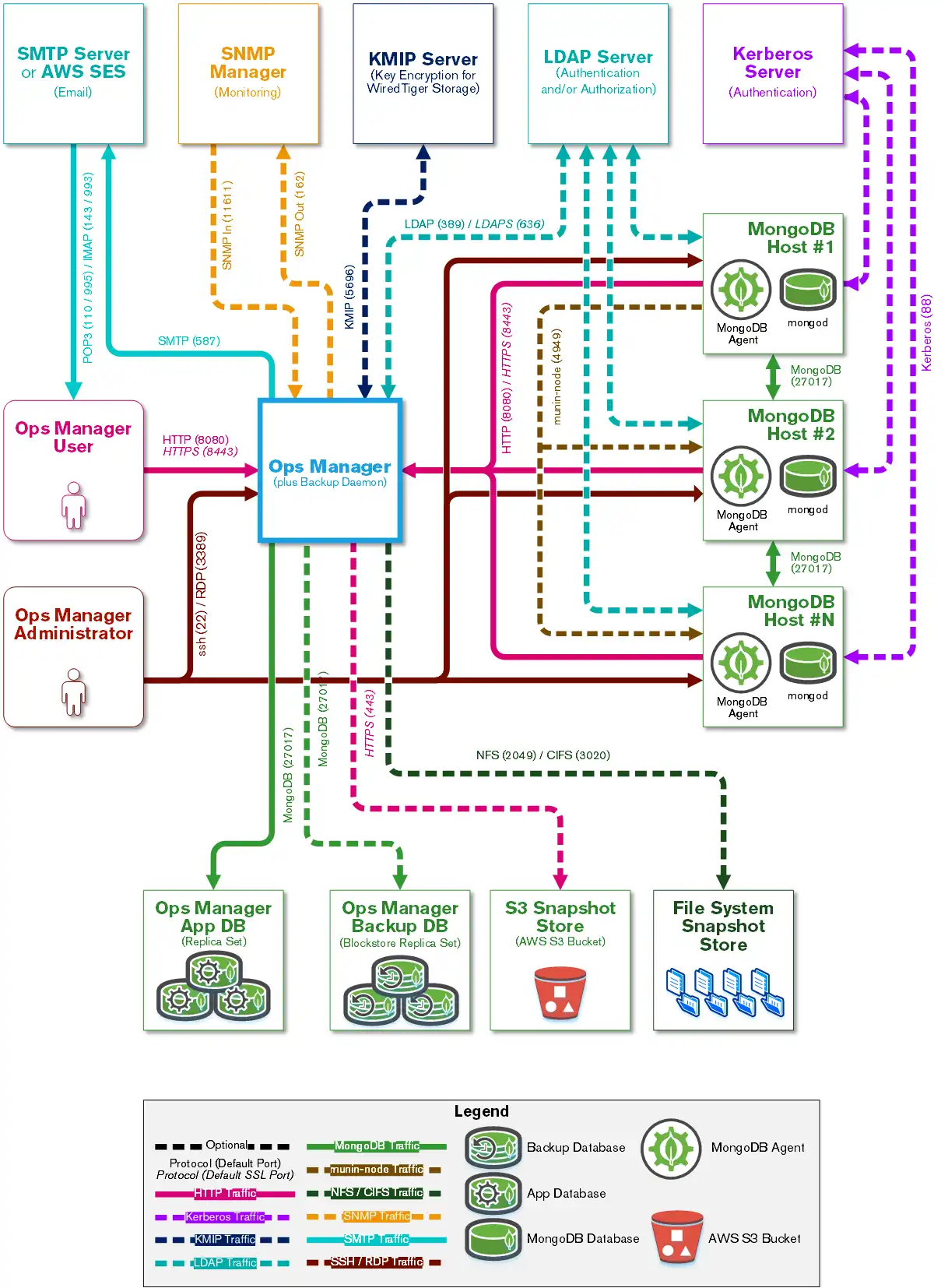
Accessible Ports
The Ops Manager Application must be able to connect to users and MongoDB Agents over HTTP or HTTPS. MongoDB Agents must be able to connect to MongoDB client MongoDB databases.
Though Ops Manager only requires open HTTP (or HTTPS) and MongoDB network ports to connect with users and to databases, what ports are opened on a firewall depend upon what capabilities are enabled: encryption, authentication and monitoring.
This page defines which systems need to connect to which ports on other systems.
Ops Manager connects with a number of services. This page explains the ports that must be opened to deploy the various components used with an Ops Manager deployment.
The specific ports that must be open on any intermediate firewalls depend upon what capabilities are enabled, such as encryption, authentication, and monitoring.
Tip
All ports listed in the following sections are either the port specified in the documentation for MongoDB installations or the known ports for the specific service assigned by the IANA. If the port number can be changed, it is noted after the table in each section.
To run Ops Manager without an Internet connection, see Configure Deployment to Have Limited Internet Access to ensure you have all of the necessary binaries to run Ops Manager without an Internet connection.
Open Ports to Access Ops Manager
Ops Manager requires the following minimum network port requirements:
Both Ops Manager users and MongoDB Agents must be able to connect to the Ops Manager application over HTTP or HTTPS.
Ops Manager must be able to connect to the mongod running the Ops Manager application MongoDB databases.
For each Ops Manager project, MongoDB Agents must be able to connect to all client MongoDB processes (
mongodormongos).The Ops Manager application must also be able to send email to Ops Manager users.
To use Ops Manager, open the following ports to the specified hosts.
Service | Default Port | Transport | Direction | Purpose | Uses TLS? | |||||
|---|---|---|---|---|---|---|---|---|---|---|
HTTP | 8080 | TCP | Inbound | Provides a web connection to Ops Manager from users and MongoDB Agents. | No | |||||
HTTPS | 8443 | TCP | Inbound | Provides a secure web connection to Ops Manager from users and MongoDB Agents. | Yes | |||||
HTTP or HTTPS | 8090 | TCP | Inbound | Provides a health-check endpoint for monitoring Ops Manager
through a monitoring service like Zabbix or Nagios. It is
only available through To enable it, see Enable the Health Check Endpoint. When enabled, you can access the endpoint at: IMPORTANT: This port is only accessible from The API endpoint provides the ability to check connections from the HTTP Service to the Ops Manager Application Database and the Backup Snapshot Storage. A successful response returns the following: | Optional | |||||
MongoDB | 27017 | TCP | Outbound | Connects to MongoDB application, backup and client databases. | Optional | |||||
SMTP | 587 | TCP | Outbound | Sends emails from Ops Manager to an SMTP host or to AWS SES. | Optional |
Note
To set a non-default port for Ops Manager, see Manage Ops Manager Hostname and Ports.
To configure a different port for the application database, see
mongo.mongoUri.To configure a different port for a client database, see Deploy a Standalone MongoDB Instance, Deploy a Replica Set, or Deploy a Sharded Cluster for a new deployment or Add Existing MongoDB Processes to Ops Manager for an existing deployment.
Open Ports to Access Ops Manager and MongoDB Hosts
Most Ops Manager administration can be performed through the user interface. Some procedures require access to the operating system. To permit your administrators to access your Ops Manager as well as MongoDB hosts, open the following ports to those hosts.
Service | Default Port | Transport | Direction | Purpose | Uses TLS? |
|---|---|---|---|---|---|
ssh | 22 | TCP | Inbound | Linux System administration. | Yes |
RDP | 3389 | TCP | Inbound | Windows System administration. | No |
Open Ports to Back Up, Restore, and Query MongoDB Instances using Ops Manager
Ops Manager can back up MongoDB databases to one or more storage systems:
A MongoDB database (blockstore)
An S3-compatible storage bucket (S3-compatible storage blockstore)
A file system (file system store).
To back up MongoDB hosts, open the following ports to the preferred backup hosts (blockstore, S3-compatible storage snapshot store and/or file system snapshot store):
Service | Default Port | Transport | Direction | Purpose | Uses TLS? |
|---|---|---|---|---|---|
MongoDB | 27017 | TCP | Outbound | Back up snapshots of entire database to blockstore or snapshot metadata to S3-compatible storage blockstore metadata database. | Optional |
HTTPS | 443 | TCP | Outbound | Back up database snapshot data to S3-compatible storage bucket. | Yes |
NFS | 2049 | TCP | Outbound | Back up database snapshots to UNIX-/Linux-based file system. | No |
CIFS | 3020 | TCP | Outbound | Back up database snapshots to Windows-based file system. | No |
Proxy Server | 25999 | TCP | Outbound | Query the snapshot backup host. | No |
Snapshots can also be restored using the link displayed in the Ops Manager application. The same ports needed to use Ops Manager would need to be open for the user to download the snapshot.
To find the download link, click Continuous Backup, then the Restore History tab, then click the download link next to the snapshot.
Note
To configure a different port for the blockstore, see Manage Blockstore Snapshot Storage.
To configure a different port for the S3-compatible storage Snapshot Store metadata database, see Manage S3 Snapshot Storage.
MongoDB 3.4.2 Enterprise and later provides the ability to query backup snapshots. Ops Manager provisions these queryable snapshots as read-only MongoDB instances, as described in Query a Backup. To query a backup snapshot, open the following ports:
Service | Default Port | Transport | Direction | Purpose | Uses TLS? |
|---|---|---|---|---|---|
MongoDB | 27700-27719 | TCP | Inbound | Enable communication between the app host and a queryable backup snapshot. | Optional |
Open Ports to Integrate Ops Manager with SNMP
Open the following ports between Ops Manager and your SNMP Manager to send and receive SNMP trap notifications from your MongoDB deployments to Ops Manager.
Important
Ops Manager 6.0.0 deprecates SNMP alerts. Ops Manager 7.0.0 will not include SNMP alerts. To learn more about other alert options, see Third-Party Service Integrations.
Service | Default Port | Transport | Direction | Purpose | Uses TLS? |
|---|---|---|---|---|---|
SNMP | 162 | UDP | Outbound | Send Traps to SNMP Manager. | No |
SNMP | 11611 | UDP | Inbound | Receive requests from SNMP Manager. | No |
Ops Manager uses community-based SNMPv2 (SNMPv2c).
Important
Ops Manager 6.0.0 deprecates SNMP alerts. Ops Manager 7.0.0 will not include SNMP alerts. To learn more about other alert options, see Third-Party Service Integrations.
You can configure the Ops Manager Application with two different types of SNMP Traps:
Trap Type | Contents | Frequency | Target |
|---|---|---|---|
Heartbeat | Internal health assessment of the Ops Manager Application | User set | one or more endpoints |
Alert | Data from a configured Ops Manager Alert | User set | one or more endpoints |
To configure the Ops Manager Application to send SNMPv2c Heartbeat or Alert Traps:
Download the MIB file.
To configure SNMPv2c Traps:
For SNMPv2c Heartbeat Traps:
Follow the Modify a Custom Setting procedure.
Set the following key/value pairs:
KeyValueNumber of seconds between heartbeat notifications.
Hosts that receive heartbeat traps on port 162.
For SNMPv2c Alert Traps:
Follow the Manage Alert Configurations procedure to configure System, Global, or Project Alerts.
Use SNMP Host as the delivery method.
Open Ports to Authenticate Ops Manager Users using LDAP
MongoDB Enterprise users can authenticate Ops Manager users using LDAP. To authenticate using LDAP, open the following ports on Ops Manager and your LDAP host.
Service | Default Port | Transport | Direction | Purpose | Uses TLS? |
|---|---|---|---|---|---|
LDAP | 389 | UDP | Both | Authenticate and/or authorize Ops Manager users against LDAP host. | No |
LDAPS | 636 | UDP | Both | Authenticate and/or authorize Ops Manager users against LDAP host. | Yes |
To configure the Ops Manager LDAP URI strings, including configuring a non-standard port, see User Authentication.
Open Ports to Authenticate with MongoDB
MongoDB Enterprise users can use Kerberos or LDAP to authenticate MongoDB users. To authenticate using LDAP or Kerberos, open the following ports between the MongoDB client databases, Ops Manager, and the Kerberos or LDAP host(s).
Service | Default Port | Transport | Direction | Purpose | Uses TLS? |
|---|---|---|---|---|---|
Kerberos | 88 | TCP / UDP | Outbound | Request authentication for MongoDB users against Kerberos host. | No |
Kerberos | 88 | UDP | Inbound | Receive authentication for MongoDB users against Kerberos host. | No |
LDAP | 389 | UDP | Both | Authenticate and/or authorize MongoDB users against LDAP host. | No |
LDAPS | 636 | UDP | Both | Authenticate and/or authorize MongoDB users against LDAP host. | Yes |
To configure Kerberos for authentication to the Ops Manager application database, see Configure Ops Manager to Authenticate with Application Databases.
Open Ports to Manage Encryption Keys using KMIP
MongoDB Enterprise deployments using the WiredTiger storage engine supports a native encryption option. You can use a KMIP service to manage the master encryption key. To support the encrypted storage engine via KMIP, open the following ports between the Backup Daemon hosts, the MongoDB hosts, and the KMIP hosts.
Service | Default Ports | Transport | Direction | Purpose | Uses TLS? |
|---|---|---|---|---|---|
KMIP | 5696 | TCP | Outbound | Send messages between MongoDB databases and KMIP host. | Yes |
Note
If you change the port for the KMIP host, see Encrypted Backup Snapshots to configure Ops Manager to use that new port.
Internet Site Access
If Ops Manager is not configured for Local Mode, it requires access to the following Internet sites over HTTPS:
Site | Purpose |
|---|---|
downloads.mongodb.com, downloads.mongodb.org | To download MongoDB Enterprise Builds. |
opsmanager.mongodb.com | To download the MongoDB version manifest. |
fastdl.mongodb.org | To download MongoDB Community Builds. |