개요
이 페이지에서는 Queryable Encryption의 보안 이점, 작동 방식, MongoDB에서 지원하는 다른 보안 메커니즘과 비교하는 방법에 대해 알아볼 수 있습니다. 또한 데이터 보안에 있어 Queryable Encryption의 가치를 보여주는 가상의 시나리오를 볼 수도 있습니다.
Queryable Encryption
Queryable Encryption을 사용하면 클라이언트 애플리케이션이 완전 무작위 암호화를 사용하여 데이터를 네트워크를 통해 전송하기 전에 데이터를 암호화하는 동시에 쿼리 기능을 유지할 수 있습니다. 민감한 데이터는 클라이언트에 의해 투명하게 암호화 및 해독되며, 암호화된 형태로만 서버와 통신합니다.
결정론적 암호화 를 사용할 수 있는 클라이언트 측 필드 레벨 암호화 와 달리 Queryable Encryption 은 구조화된 암호화 를 기반으로 하는 빠르고 검색 가능한 암호화 체계를 사용합니다. 이러한 체계는 동일한 일반 텍스트 입력이 제공되더라도 서로 다른 암호화됨 출력 값을 생성합니다.
Queryable Encryption은 어떻게 작동하나요?
아래 다이어그램은 고객 환경에서 Queryable Encryption이 어떻게 사용되는지 그 과정과 아키텍처를 보여 줍니다.
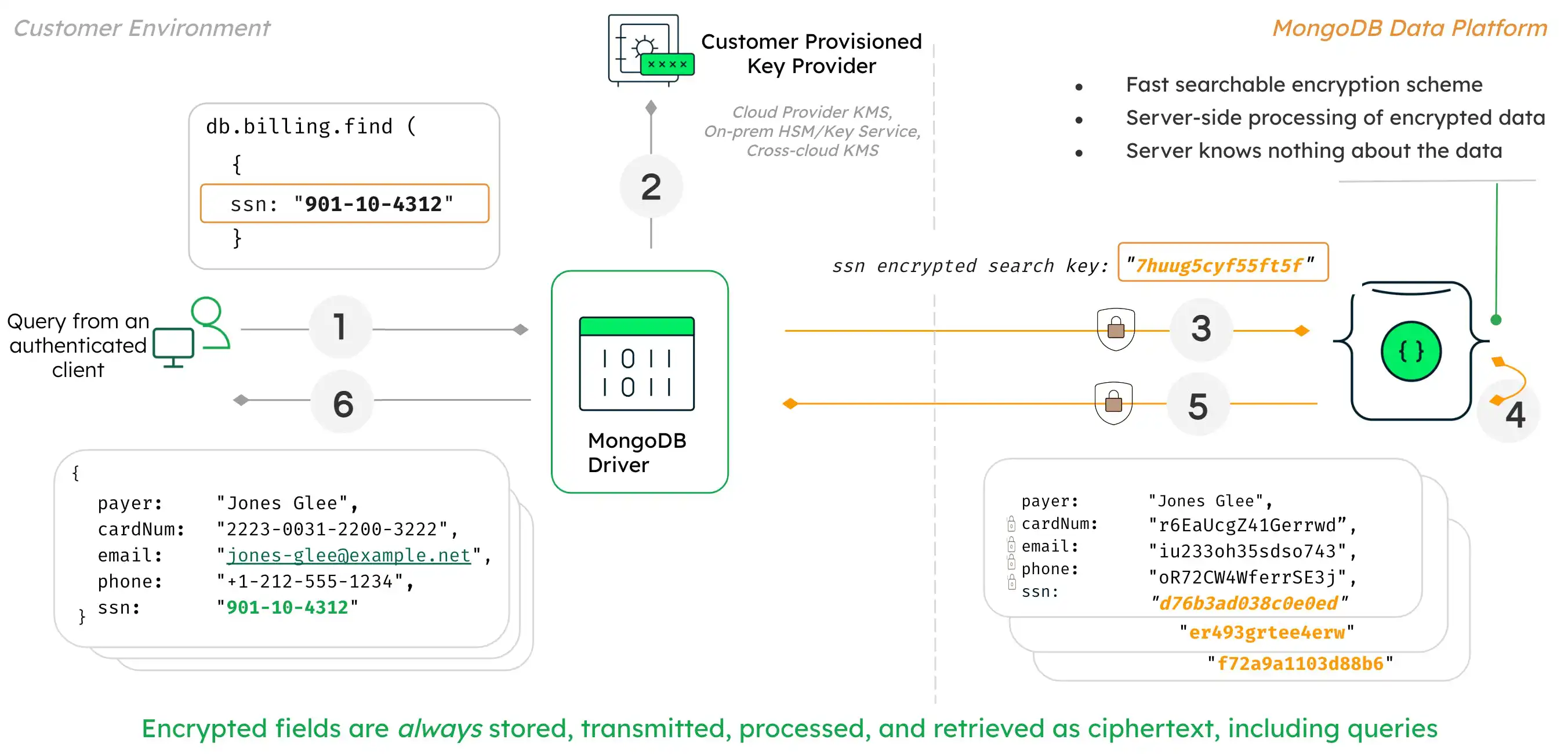
이 다이어그램에서 사용자는 SSN 번호와 같이 완전히 무작위로 암호화된 데이터를 쿼리할 수 있습니다.
Queryable Encryption 내에서 이를 가능하게 하는 프로세스와 메커니즘은 다음과 같습니다.
애플리케이션이 쿼리를 제출하면 MongoDB 드라이버가 먼저 쿼리를 분석합니다.
드라이버는 쿼리가 암호화된 필드에 대한 것임을 인식하고 고객이 프로비저닝한 키 제공업체에 암호화 키를 요청합니다.
AWS Key Management Service(AWS KMS)
Google Cloud KMS
Azure Key Vault
모든 KMIP호환 키 제공자
드라이버는 암호문으로 렌더링된 암호화된 필드와 함께 MongoDB 서버에 쿼리를 제출합니다.
Queryable Encryption은 서버가 데이터에 대해 아무것도 모른 채 완전히 암호화된 데이터에 대한 쿼리를 처리할 수 있는 빠르고 검색 가능한 체계를 구현합니다. 데이터와 쿼리 자체는 서버에서 항상 암호화된 상태로 유지됩니다.
MongoDB 서버는 쿼리의 암호화된 결과를 드라이버에 반환합니다.
쿼리 결과는 드라이버가 보유한 키로 해독되어 클라이언트에 반환되고 일반 텍스트로 표시됩니다.
다음 데이터 구조의 도움으로 Queryable Encryption 기능을 사용할 수 있습니다. 이를 수정하거나 삭제하지 않으면 쿼리 결과가 부정확해질 수 있으므로 주의해야 합니다.
Queryable Encryption은 Queryable Encryption 암호화된 필드가 있는 모든 collection의 문서에
__safeContent__필드를 추가합니다.Queryable Encryption는 Queryable Encryption로 암호화된 필드가 있는 컬렉션과 동일한 데이터베이스에 두 개의 내부 메타데이터 컬렉션을 생성합니다. 이 컬렉션의 이름은 다음과 같습니다.
enxcol_.<collectionName>.escenxcol_.<collectionName>.ecoc
경고
이러한 데이터 구조를 수정하지 마십시오. 그렇지 않으면 쿼리 결과가 올바르지 않고 보안에 영향을 미칠 수 있습니다.
Queryable Encryption는 다음 시나리오에서 암호화된 필드를 안전하게 유지합니다.
데이터베이스 슈퍼유저가 암호화된 필드에 직접 액세스
서버의 메모리를 읽어 암호화된 필드에 액세스
안전하지 않은 네트워크를 통해 암호화된 필드 캡처
데이터베이스 또는 백업 파일을 읽어 온디스크 암호화된 필드에 액세스합니다.
암호화된 필드가 있는 문서의 패턴을 식별하여 공격하는 빈도 분석
모든 클라이언트는 민감하지 않은 데이터 필드에 액세스할 수 있지만, 적절하게 구성된 Queryable Encryption 클라이언트만 암호화된 데이터 필드를 사용하여 읽기 및 쓰기 쿼리를 실행할 수 있습니다.
중요
원격 키 관리 시스템
프로덕션에서 Queryable Encryption을 사용하는 경우 원격 키 관리 시스템(KMS)을 사용하여 암호화 키를 저장해야 합니다.
Queryable Encryption 과 함께 원격 KMS 사용하는 방법을 보여주는 단계별 가이드 보려면 Queryable Encryption 튜토리얼을 참조하세요.
지원되는 모든 KMS 제공자 목록을 보려면 KMS 제공자를 참조하세요.
원격 KMS를 사용해야 하는 이유에 대해 자세히 알아보려면 Reasons to Use a Remote Key Management System(원격 키 관리 시스템을 사용하는 이유)를 참조하세요.
기타 보안 메커니즘
이 섹션에서는 MongoDB에서 지원하는 다음 보안 메커니즘에 대해 설명하고 사용 사례와 제한 사항을 설명합니다.
역할 기반 액세스 제어
역할 기반 액세스 제어는 관리자가 사용자에게 컬렉션 수준의 권한을 부여하고 제한할 수 있는 보안 메커니즘입니다. 이 솔루션은 적절한 역할 정의 및 할당을 통해 실수로 데이터 및 액세스 권한이 공개되는 것을 방지합니다.
역할 기반 액세스 제어는 다음과 같은 시나리오를 보호할 수 없습니다.
안전하지 않은 네트워크를 통한 데이터 캡처
데이터베이스 또는 백업 파일을 읽어 온디스크 데이터에 액세스
서버의 메모리를 읽어서 데이터 액세스
데이터베이스 슈퍼유저가 데이터에 직접 액세스
자세한 내용은 역할 기반 액세스 제어를 참조하세요.
저장된 데이터 암호화
미사용 데이터 암호화는 디스크의 데이터베이스 파일을 암호화하는 메커니즘입니다. 이 메커니즘은 데이터베이스 자격 증명이 없지만 데이터베이스를 호스팅하는 컴퓨터에 액세스할 수 있는 사람이 데이터를 볼 수 없도록 합니다.
이 메커니즘은 다음과 같은 시나리오에 대해서는 데이터를 보호하지 않습니다.
안전하지 않은 네트워크를 통한 데이터 캡처
서버의 메모리를 읽어서 데이터 액세스
데이터베이스 슈퍼유저가 데이터에 직접 액세스
자세한 내용은 미사용 데이터 암호화를 참조하세요.
전송 암호화(TLS/SSL)
TLS/SSL을 사용한 전송 암호화는 네트워크를 통해 데이터를 암호화합니다. TLS/SSL은 안전하지 않은 네트워크를 통해 이동하는 데이터를 보호하지만, 권한이 있는 사용자로부터 데이터를 보호하거나 디스크에 저장된 데이터를 보호할 수는 없습니다.
자세히 알아보려면 TLS/SSL을 사용한 전송 암호화를 참조하세요.
기능 비교
클라이언트측 필드 수준 암호화에 대해 자세히 알아보려면 클라이언트 사이드 필드 레벨 암호화 기능을 참조하세요.
다음 표에서는 잠재적인 보안 위협과 MongoDB 암호화 기능이 이를 주소 하는 방법을 설명합니다. 역할 기반 액세스 제어, 미사용 데이터 암호화, 전송 암호화 및 사용 중 암호화 메커니즘을 함께 사용합니다. 동일한 컬렉션 에서 클라이언트 측 필드 레벨 암호화 와 Queryable Encryption 을 모두 사용할 수는 없습니다.
중요
이는 일반적인 비교를 위한 높은 수준의 요약입니다. 자세한 내용은 Queryable Encryption 개요 및 상태 비저장 문서 데이터베이스 암호화 체계의 설계 및 분석 백서를 참조하세요.
위협 | TLS/SSL 전송 암호화 | 미사용 데이터 암호화(EaR) | Queryable Encryption (Equality) + TLS/SSL + EaR | CSFLE + TLS/SSL + EaR |
|---|---|---|---|---|
네트워크 스누핑(공격자가 네트워크 트래픽에 액세스 수 있음) | 작업 메타데이터표시 | 작업 메타데이터 표시 | 작업 메타데이터 표시 | 작업 메타데이터 표시 |
디스크에서 데이터베이스 복구(공격자가 물리적 디스크 액세스 있음) | 데이터베이스 표시 | 데이터베이스 및 작업 메타데이터 의 크기 표시 | 데이터베이스 및 작업 메타데이터 의 크기 표시 | 데이터베이스 및 작업 메타데이터 의 크기 표시 |
데이터베이스 표시 | 데이터베이스 표시 | 데이터베이스 및 작업 메타데이터 의 크기 표시 | 값 및 작업 메타데이터 의 빈도를 표시합니다. | |
지능형 지속적 위협 (공격자는 탐지되지 않은 상태에서 네트워크, 디스크, 메모리에 장기간 지속적으로 액세스 함) | 데이터베이스 표시 | 데이터베이스 표시 | Queryable Encryption ATP로부터 보호하도록 설계되지 않았습니다. 자세한 내용은 백서를 참조하세요. | CSFLE는 ATP로부터 보호하도록 설계되지 않았습니다. 자세한 내용은 백서를 참조하세요. |
| [1] | 여기서는 완료된 작업 사이에 유출이 발생한다고 가정합니다. 자세한 내용은 백서를 참조하세요. |
경고
Queryable Encryption 은 환경에 지속적으로 액세스 하는 공격자나 데이터베이스 스냅샷과 함께 제공되는 쿼리 기록/로그를 모두 조회 할 수 있는 공격자가 아닌 데이터 유출로부터 보호합니다.
Queryable Encryption 사용할 때 동일성 및 범위 쿼리는 데이터베이스 스냅샷을 통해 공격자에 대해 유사한 보안을 제공합니다. 그러나 데이터베이스 스냅샷과 쿼리 정보 모두에 액세스 할 수 있는 공격자는 Queryable Encryption의 보안이 보장 범위를 벗어납니다. 이는 범위 쿼리의 경우 특히 조회되는 쿼리 기록이나 로그 수가 적은 경우에도 마찬가지입니다. 자세한 내용은 개요 백서에서 6.1: 영구 모델의 쿼리 범위 를 참조하세요.
Scenario
다음 가상의 시나리오는 애플리케이션의 데이터를 보호하는 데 있어 Queryable Encryption의 가치와 이 가이드에서 설명하는 다른 보안 메커니즘과 Queryable Encryption이 상호 작용하는 방식을 보여줍니다.
이 시나리오에서는 가상의 회사 MedcoMD의 환자 개인 정보, 청구 정보 및 의료 기록을 저장하는 의료 관리 시스템에서 민감한 데이터를 보호합니다. 환자 데이터는 공개되지 않으며, 사회보장번호(SSN, 미국 정부에서 발급한 주민등록번호), 환자 ID 번호, 청구 정보, 약물 정보와 같은 특정 데이터는 특히 민감하며 개인정보 보호 규정 준수의 대상이 됩니다. 데이터가 비공개로 안전하게 유지되는 것은 회사와 환자에게 중요합니다.
MedcoMD는 다음 사용 사례를 충족하기 위해 이 시스템이 필요합니다.
의사는 이 시스템을 사용하여 환자의 의료 기록, 청구 정보에 액세스하고 약물을 업데이트합니다.
접수 담당자는 시스템을 통해 연락처 정보를 사용하여 환자의 신원을 확인합니다.
접수 담당자는 환자의 청구 정보를 볼 수 있지만 환자 ID 번호는 볼 수 없습니다.
접수원은 환자의 의료 기록에 액세스할 수 없습니다.
MedcoMD는 또한 다음과 같은 방법을 통한 민감한 데이터의 공개를 염려하고 있습니다.
접수 담당자가 공개적으로 볼 수 있는 화면에서 실수로 데이터를 공개하는 경우.
데이터베이스 관리자와 같은 슈퍼유저가 데이터베이스에 직접 접근합니다.
안전하지 않은 네트워크를 통한 데이터 캡처입니다.
데이터베이스 서버의 메모리를 읽어 데이터에 액세스합니다.
데이터베이스 또는 백업 파일을 읽어 데이터에 액세스합니다.
의료 서비스 관리 시스템의 기능과 액세스 제한의 균형을 맞추려면 MedcoMD는 무엇을 할 수 있을까요?
솔루션
MedcoMD는 다음과 같은 보안 메커니즘을 사용하여 사용 사례를 충족하고 민감한 의료 데이터의 공개를 방지합니다.
네트워크를 통해 이동하는 데이터를 보호하기 위한 전송 암호화(TLS/SSL)
데이터베이스 또는 백업 파일을 읽음으로써 데이터가 유출되지 않도록 보호하기 위한 미사용 데이터 암호화입니다.
역할 기반 액세스 제어를 통해 데이터베이스 사용자의 액세스를 작업 수행에 필요한 컬렉션으로 제한합니다.
Queryable Encryption을 통해 민감한 필드를 암호화하여 다음 사용 사례 및 제약 조건을 충족합니다.
Queryable Encryption 암호화 데이터는 암호화되지 않은 형태로 데이터베이스 서버에 저장되지 않으므로 서버 메모리에서 데이터를 읽지 못하도록 합니다.
접수 담당자에게 Queryable Encryption이 활성화되지 않은 클라이언트를 제공하여, 접수 담당자가 공개적으로 볼 수 있는 화면에서 환자의 신원을 확인하고 민감한 데이터가 실수로 노출되는 것을 방지합니다.
의사에게 Queryable Encryption이 활성화된 클라이언트를 제공하여 의사가 진료실에서 민감한 데이터를 비공개로 볼 수 있도록 하세요.
자세히 알아보기
MongoDB 배포를 보호하기 위해 구현해야 하는 보안 조치 목록을 보려면 Security Checklist(보안 체크리스트)를 참조하세요.
Queryable Encryption 사용을 시작하려면 Queryable Encryption 빠른 시작을 참조하세요.