MongoDB & HashiCorp Vault
Simplify secrets management
Standardize and control workflows
Cloud-first and platform agnostic
How to use MongoDB Atlas and HashiCorp Vault
Sign up for MongoDB Atlas
If you don’t already use MongoDB Atlas, sign up for an account today. Distributed and secure by default, MongoDB Atlas is a global cloud database service available on AWS, Azure, and Google Cloud.
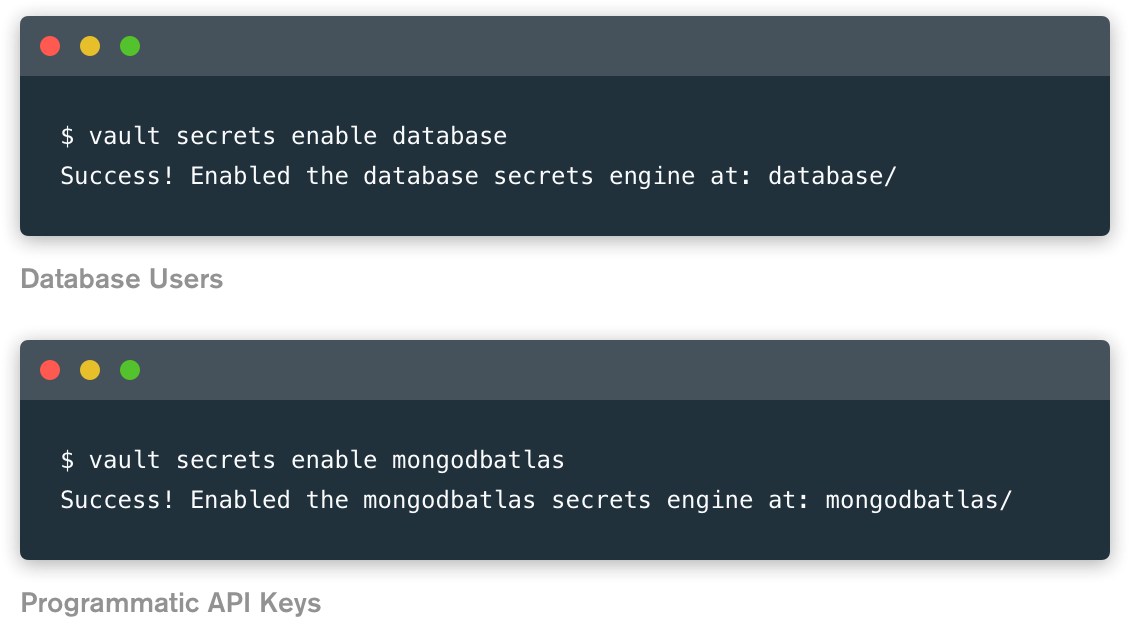
Enable the Secrets Engine(s)
The MongoDB Atlas Secrets Engines are available with Vault 1.4 or higher. To get started, simply enable one or both of the Secrets Engines in Vault.
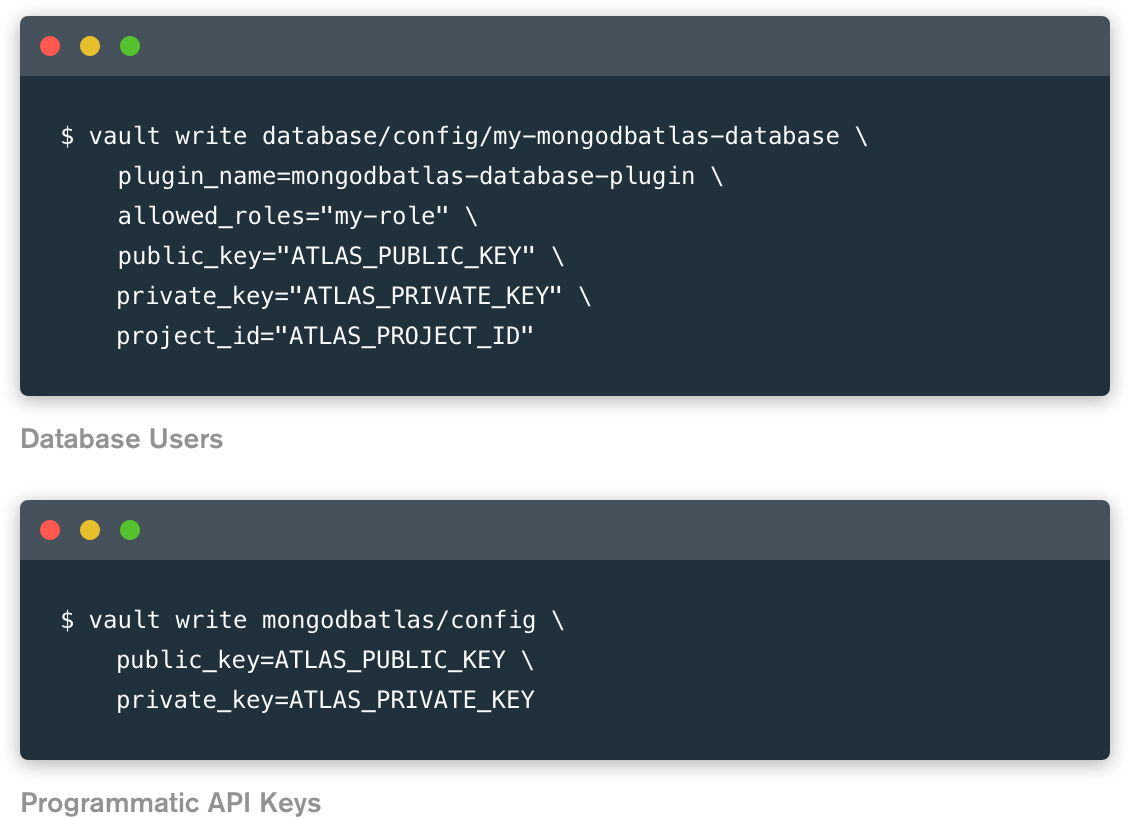
Configure Vault
Once you have enabled a Secret Engine, you will need to configure Vault with the proper plugin and connection information.
Manage secrets with Vault
Once you’ve created your MongoDB Atlas account and configured the secrets engines, you’re all set! You can now create, manage, and update Atlas database users and programmatic API keys in HashiCorp Vault.
Customers Using HashiCorp Vault & MongoDB Atlas
MongoDB Atlas & HashiCorp Vault FAQ
What is MongoDB Atlas?
MongoDB Atlas is the global cloud database service for modern applications. Deploy fully managed MongoDB across AWS, Azure, or Google Cloud with best-in-class automation and proven practices that guarantee availability, scalability, and compliance with security standards. Use MongoDB’s robust ecosystem of drivers, integrations, and tools to build faster and spend less time on operations and database administration.
With Atlas, you can easily create and manage dynamic database user and programmatic API key access through HashiCorp Vault.
Can I use HashiCorp Vault with my existing MongoDB database?
If you are running a non-Atlas MongoDB deployment, you can use the MongoDB Database Secrets Engine (which was created by the Vault team), to allow users to create and manage database credentials dynamically based on configured roles for self-managed MongoDB deployments.
If you are using MongoDB Enterprise Advanced, Vault also offers a KMIP Secrets Engine that is only available to Vault Enterprise customers. This plugin “allows Vault to act as a KMIP server for clients that retrieve cryptographic keys for encrypting data via KMIP protocol.” MongoDB Enterprise Advanced customers can use this integration to manage KMIP-managed objects; For more information, check out HashiCorp’s tutorial on how to set up and use this secrets engine.
With the two new MongoDB Atlas Secrets Engines for HashiCorp Vault, you will be using official plugins approved by HashiCorp and included in the Vault binary, starting in version 1.4. You will also have access to customer support from MongoDB (if you have an Atlas Developer or higher support plan).
What is HashiCorp Vault?
Vault is a secrets management tool by HashiCorp. It enables teams to centrally manage and distribute secrets (such as tokens, passwords, certificates, and encryption keys) and other sensitive data through a UI, CLI, or HTTP API.
Vault has a free, open source offering as well as an enterprise version, which includes advanced features to support collaboration, governance, and multiple datacenters. Vault offers integrations with many popular identity providers, including cloud IAM platforms, Kubernetes, and Active Directory, and supports both public clouds and private datacenters with a broad range of endpoint systems, including databases, cloud platforms, messaging queues, SSH, and more.
Who is HashiCorp?
HashiCorp is a cloud infrastructure automation software company whose suite of tools enable organizations to provision, secure, connect, and run any infrastructure for any application. HashiCorp is the creator of the tools Vagrant, Packer, Terraform, Vault, Consul and Nomad. The HashiCorp suite unlocks the cloud operating model for every business and enables their digital transformation strategies to succeed.
What is a Secrets Engine in HashiCorp Vault?
In order for Vault to manage secrets across different services and platforms, customers must use secrets engines: “Secrets engines are components which store, generate, or encrypt data.” The exact functionality of a secrets engine varies depending on what it is for - for example, database secrets engines are essentially plugins that can generate database credentials dynamically based on configured roles.
Secrets engines behave similar to a virtual filesystem, and can be enabled, disabled, tuned, and moved via the CLI or API in Vault. Secrets engines are available for cloud platforms (e.g., AWS, Azure, Google Cloud), databases (e.g., Cassandra, MySQL, PostgreSQL), SSH, and other secrets types. Most secrets engines are created and supported by HashiCorp.
What are the MongoDB Atlas Secrets Engines for HashiCorp Vault?
There are two official, HashiCorp-approved MongoDB Atlas Secrets Engines:
The MongoDB Atlas Secrets Engine generates unique, ephemeral programmatic API keys for MongoDB Atlas with assigned roles and permissions, along with IP whitelists to restrict individual key access. Project IP whitelists in Atlas do not cover API keys, so each API key must have an associated IP whitelist.
The MongoDB Atlas Database Secrets Engine generates unique, ephemeral database users for MongoDB Atlas projects, which can be managed programmatically in HashiCorp Vault. This secrets engine already existed for self-managed MongoDB users, but we made a new secrets engine to support MongoDB Atlas customers.
These two secrets engines can be used independently or together to help manage database security and access for MongoDB Atlas.
Who is supporting the MongoDB Atlas Secrets Engines for HashiCorp Vault?
The MongoDB Atlas Secrets Engines code is hosted by MongoDB, so community members are welcome to contribute to the project and report or submit bug fixes. MongoDB will maintain and update the MongoDB Atlas Secrets Engines as required and as engineering resources are available.
The MongoDB Cloud Support team will be available to help troubleshoot any issues related to MongoDB Atlas Secrets Engines for HashiCorp Vault as part of a customer’s current support contract (for Atlas Developer plans and higher).
I’m interested in using HashiCorp Vault to manage other secrets for MongoDB Atlas. What should I do?
Let us know! Click here to leave feedback (select "Vault plugin" as the category in your submission).
How is HashiCorp Vault different from other secrets management tools?
HashiCorp Vault is often listed alongside Credstash, Keywhiz, AWS Secrets Manager, and other tools under the category of secrets management. A secrets manager is exactly what it sounds like: a tool that allows you to securely store and manage secrets. However, tools vary in what specific functionality they actually provide. Some tools include version history, while others take care of leasing or complex ACL lists. As such, it’s often easier to compare two specific tools at a time, rather than all of them at the same time.
HashiCorp Vault is generally regarded as one of the most comprehensive secrets management tools due to its cloud-native and platform-agnostic approach. Tools like Credstash, for example, require AWS services like AWS KMS in order to work. Similarly, AWS Secrets Manager and GCP Secrets Manager require AWS KMS and Google KMS, respectively, to work. HashiCorp Vault is most similar to Keywhiz, but has more features and the backing of a company, rather than being an open source project created by Square. It’s also deeply integrated with the rest of the HashiCorp stack.
For more information on how HashiCorp Vault compares to other secrets management tools, see their documentation here.
How is HashiCorp Vault different from a KMS?
A KMS (Key Management Service) is a specific type of secrets management program that encrypts data and returns the encrypted ciphertext. Normally, a KMS does not store the secret itself, just the keys to encrypt or decrypt it.
KMS systems may do some management via Key Management Interoperability Protocol (KMIP), but most KMS products that support KMIP aren’t cloud native. HashiCorp Vault Enterprise recently became KMIP-compliant, but in general companies have switched to cloud-native secrets managers to better manage their cloud infrastructure and applications.
HashiCorp Vault offers KMS functionality while also serving other secrets management functions such as dynamic secrets, on-demand credentials for fine-grained security controls, auditing, and non-repudiation. In addition to being more comprehensive as a tool, it’s also cloud- and platform-agnostic, freeing customers from lock-in.
For more information on how HashiCorp Vault compares to other secrets management tools, see their documentation here.