As MongoDB Atlas adoption grows across large organizations, Atlas projects increasingly sit at the intersection of multiple teams: platform engineering, security, operations, site reliability engineering (SRE), and application teams. Each group requires access to Atlas to perform specific operational tasks, such as scaling clusters, creating indexes, managing backups, or reviewing logs. Empowering these teams is essential to completing these tasks. Concurrently, inheritance of unnecessary privileges must be avoided to reduce risk.
To date, customers have faced an uncomfortable tradeoff. To enable teams to perform specific operational tasks, organizations often had to grant broad, highly privileged roles. In some cases, this access was provided only temporarily, such as assigning the project Owner role to rotate database credentials or update network access. Alternatively, organizations have denied access entirely (zero trust) and routed requests through a small set of administrators. For enterprises operating under strict security and compliance requirements, these approaches:
Create friction
Increase operational overhead
Force compromises on least-privilege principles
For smaller teams, ambiguity regarding which roles to assign can lead to over-permissioning early in the Atlas journey.
To address these challenges, MongoDB is introducing a set of fine-grained, purpose-built user roles at the Atlas project level. These roles enable platform teams and project owners to securely delegate Atlas UI and API access for common operational tasks without exposing sensitive settings, access management capabilities, or data. The result is a simpler, safer way to scale access to Atlas while strengthening an organization's security posture through centralized control.
User roles in MongoDB Atlas
User roles in MongoDB Atlas define what actions a user, team, API key, or service account is permitted to perform in an Atlas organization or project. Roles are the foundation of access control in Atlas. They determine who can view, create, modify, or operate resources such as clusters, indexes, backups, alerts, and network settings.
Prior to this launch, Atlas offered a smaller set of broader roles designed to cover a wide range of functional areas. Throughout 2025, MongoDB has expanded this approach by introducing several fine-grained roles in response to customer feedback. These have subsequently experienced positive adoption. While effective for centralized administration, the original roles often bundled permissions that did not align with real-world responsibilities. This forced customers to either over-provision access for a single task or build custom controls to constrain user actions.
New granular, purpose-built Atlas user roles
The new Atlas user roles are designed around common ‘real-world’ operational use cases observed across enterprise and mid-market customers. Each role grants a narrowly scoped set of permissions aligned to a specific function. These include managing indexes, restoring backups, testing resilience, or configuring alerts. All roles adhere to least-privilege principles and can be combined using Atlas teams and groups to align with an organization’s internal operating model.
These roles enable the direct delegation of operational responsibilities in Atlas through both the UI and APIs without relying on over-privileged roles or external tooling. The following table provides an overview of seven of the new user roles now available in Atlas. For details on all fifteen new roles, read the expanded documentation.
Figure 1. Create a new user in an Atlas project and assign them granular, purpose-built roles to govern access.
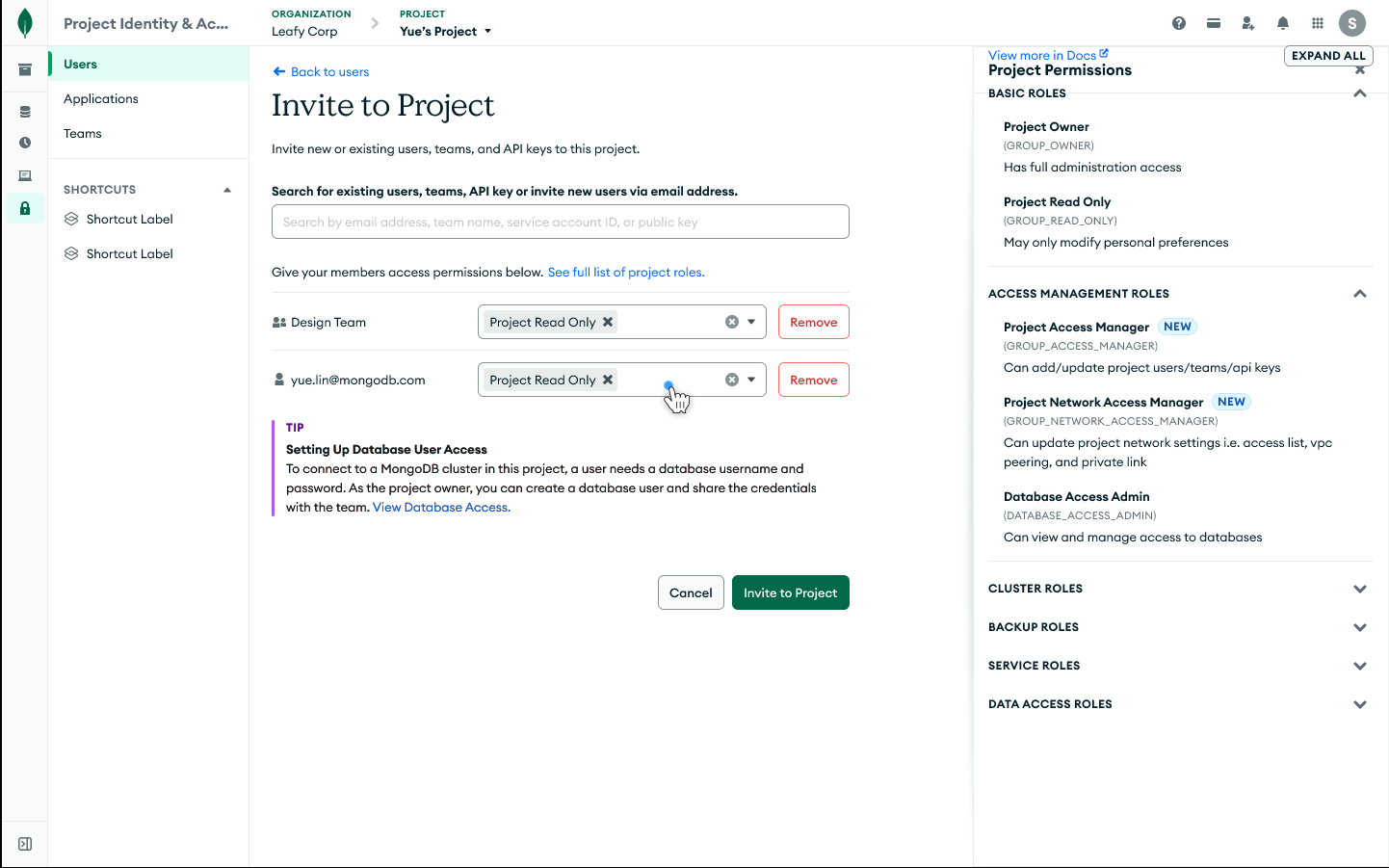
Figure 2. Edit an existing user’s role in an Atlas project to ensure they have the necessary permissions.
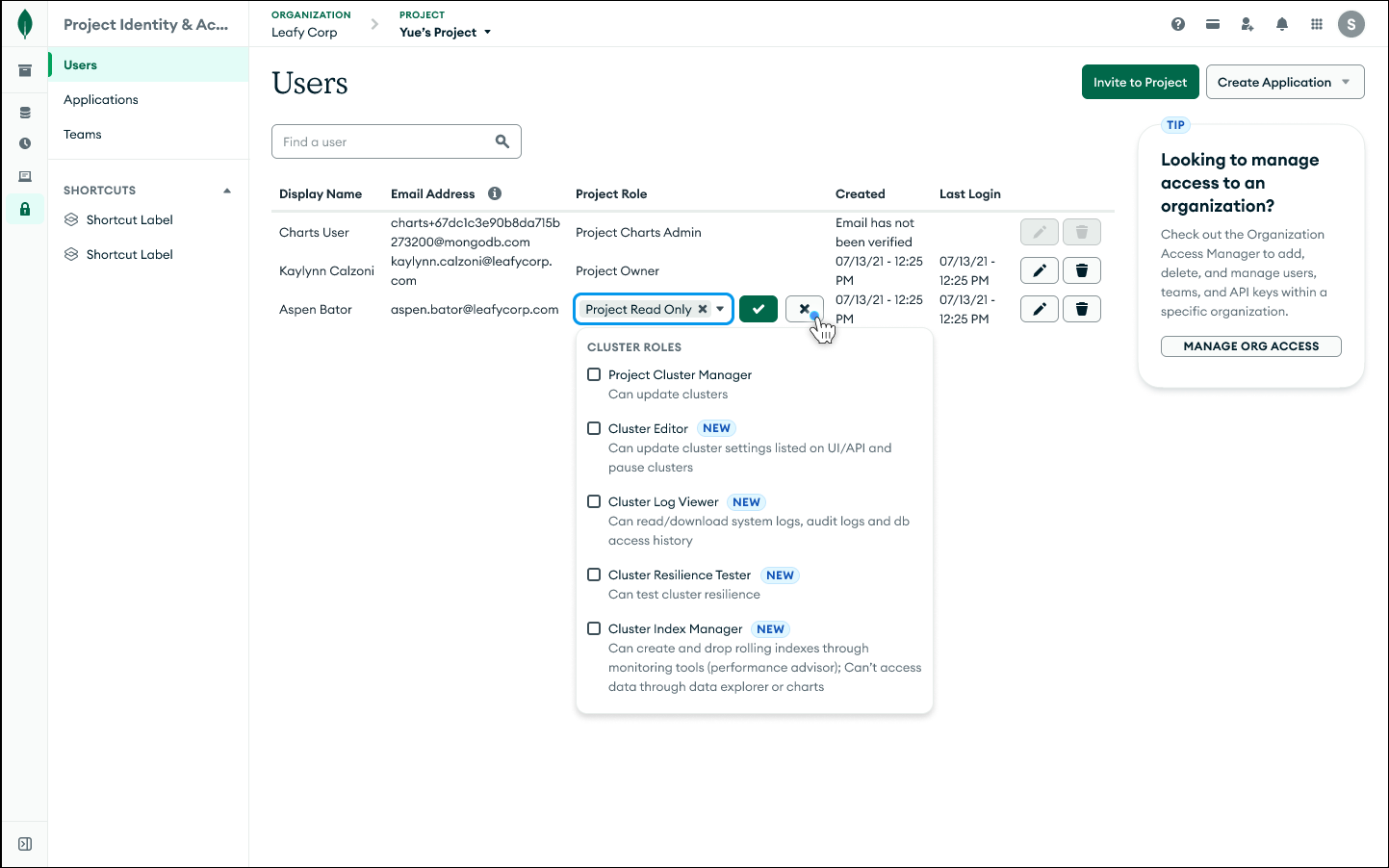
Figure 3. Create a new API key and assign it specific roles to granularly govern access and ensure least privilege.
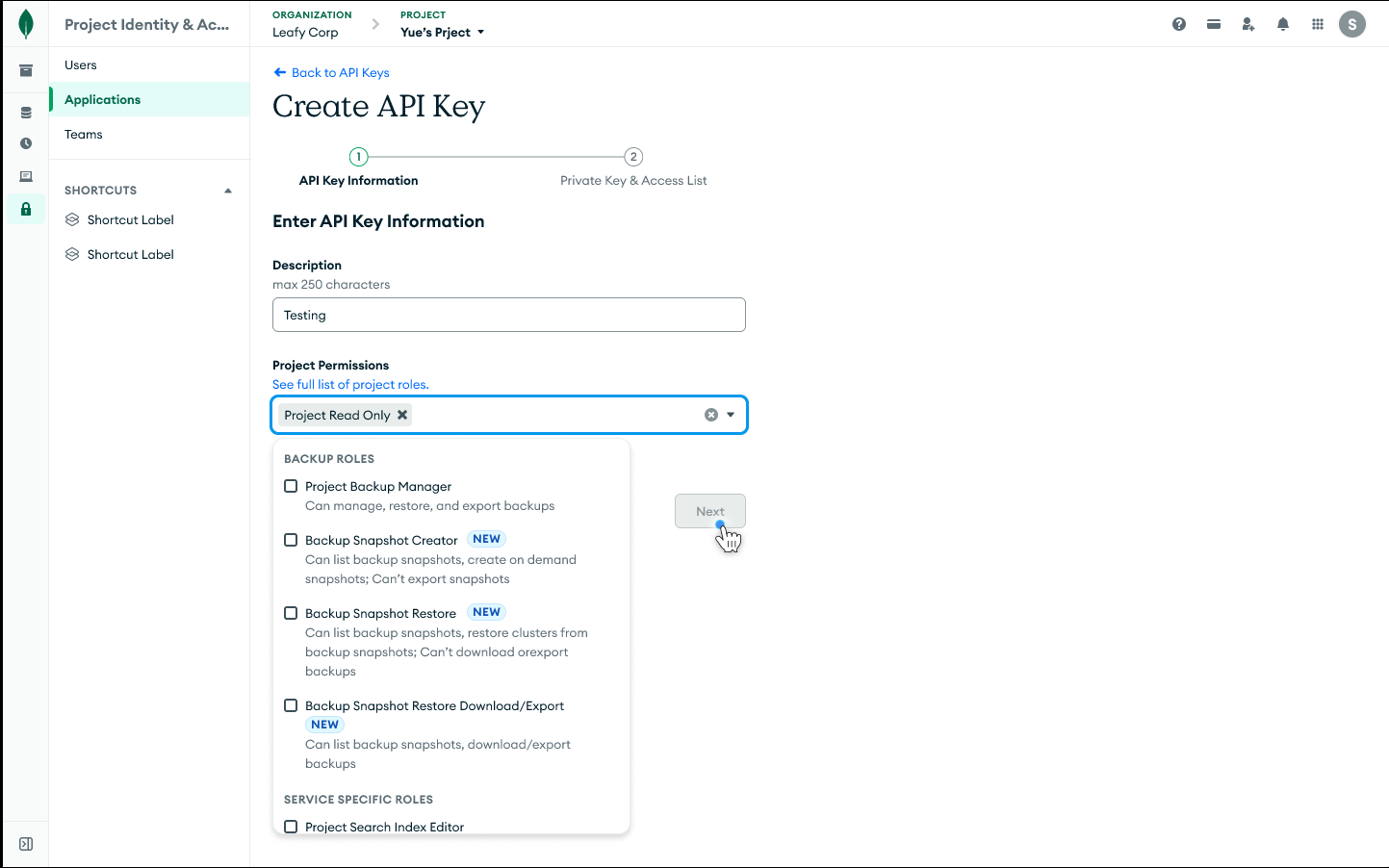
What purpose-built user roles unlock for Atlas customers
MongoDB Atlas customers gain immediate access to a number of benefits from these new user roles, including:
True least-privilege access
An immediate benefit of these new roles is the ability to apply least-privilege access consistently across Atlas projects. Instead of granting broad administrative roles to enable a single task, organizations can now assign narrowly scoped permissions that align directly with job responsibilities. This reduces the risk of compromised credentials and supports zero-trust security architectures.
Secure delegation without custom control planes
Many customers, particularly in regulated industries, have built internal control planes or automation layers to limit how Atlas is used. The new roles reduce or eliminate the need for these workarounds by enabling safe delegation directly in Atlas. Platform teams can continue to automate baseline provisioning and governance, while empowering operations and product teams to use Atlas UI features for day-to-day work.
Safer operations in regulated environments
For enterprises subject to compliance requirements, these roles unlock operational capabilities that were previously difficult or impossible to grant. Teams can test resilience, restore backups, manage network access, or review audit logs without inheriting permissions to modify access controls or interact with production data. This separation of duties supports internal audit requirements and regulatory expectations.
Reduced over-permissioning for integrations and automation
API keys and service accounts often require elevated privileges simply to perform a narrow function. These include exporting backups or managing indexes. Granular roles enable these integrations to operate with only the necessary permissions. This reduces security risks and simplifies compliance reviews.
Democratizing access to the Atlas UI
Atlas provides rich operational insights and tooling through its UI. However, many organizations have historically restricted access due to security concerns. With purpose-built roles, more teams can safely use Atlas UI features. These include Performance Advisor, alerting, and real-time performance tools. Additionally, this can be done without exposing sensitive controls. This improves operational efficiency while maintaining strong governance.
Get started with new Atlas user roles
The new granular user roles are available directly in MongoDB Atlas and can be assigned to users, teams, API keys, and service accounts at the project level. Roles can be combined using Atlas teams to reflect internal job functions, simplifying access management at scale. Read the documentation to get started.
Organizations can begin by identifying common operational tasks currently restricted by overly privileged roles. These can be replaced with purpose-built, more effective alternatives. Over time, this approach standardizes access patterns, reduces security risk, and enables teams to work independently across Atlas.
By aligning access control with real operational needs, these new Atlas user roles enable organizations to scale MongoDB securely without sacrificing agility or compliance.